

Allegedly allegedly allegedly
- The Onion
I like computers, trains, space, radio-related everything and a bunch of other tech related stuff. User of GNU+Linux.
I am also dumb and worthless.
My laptop is ThinkPad L390y running Arch.
I own RTL-SDRv3 and RSP1 clone.
SDF Unix shell username: user224


Allegedly allegedly allegedly


Sorry about my Waypipe misunderstanding.
vncserver I configured that way, so of course. I just didn’t expect it to connect to Wayland.
If invoking xfce4-session works, it means you are doing so over vnc, not waypipe.
It does work over Waypipe. You can even see in my screenshot that on the remote machine it shows Waypipe as the WM.
The remote is running Debian 13, with multi-user.target set as default target to keep the GUI from starting. XFCE version is 4.20.1.


Using Waypipe, which proxies Wayland program GUIs to my local computer, just like ssh -X, but with Wayland, and it actually works over the internet (read: high latency).
I didn’t know XFCE supported Wayland , so I casually ran vncserver, which launched xfce4-session, except that it attached itself to the Wayland display (proxied to my local machine) rather than X display of TigerVNC. And here come the full XFCE right to my local machine (which is running Plasma).


Only if the machine is on LAN. I am running with 250ms here.


No, I was not using VNC. VNC xstartup script just launched xfce4-session which connected to Waypipe rather than Xtigervnc.
It does integrate itself to KDE nicely. Even with virtual desktops. And it even properly does the animations. Downside is, I can’t access the original desktop on my laptop while it’s running. Peek at desktop also shows XFCE.
Here’s the cube switcher, showing XFCE instead:
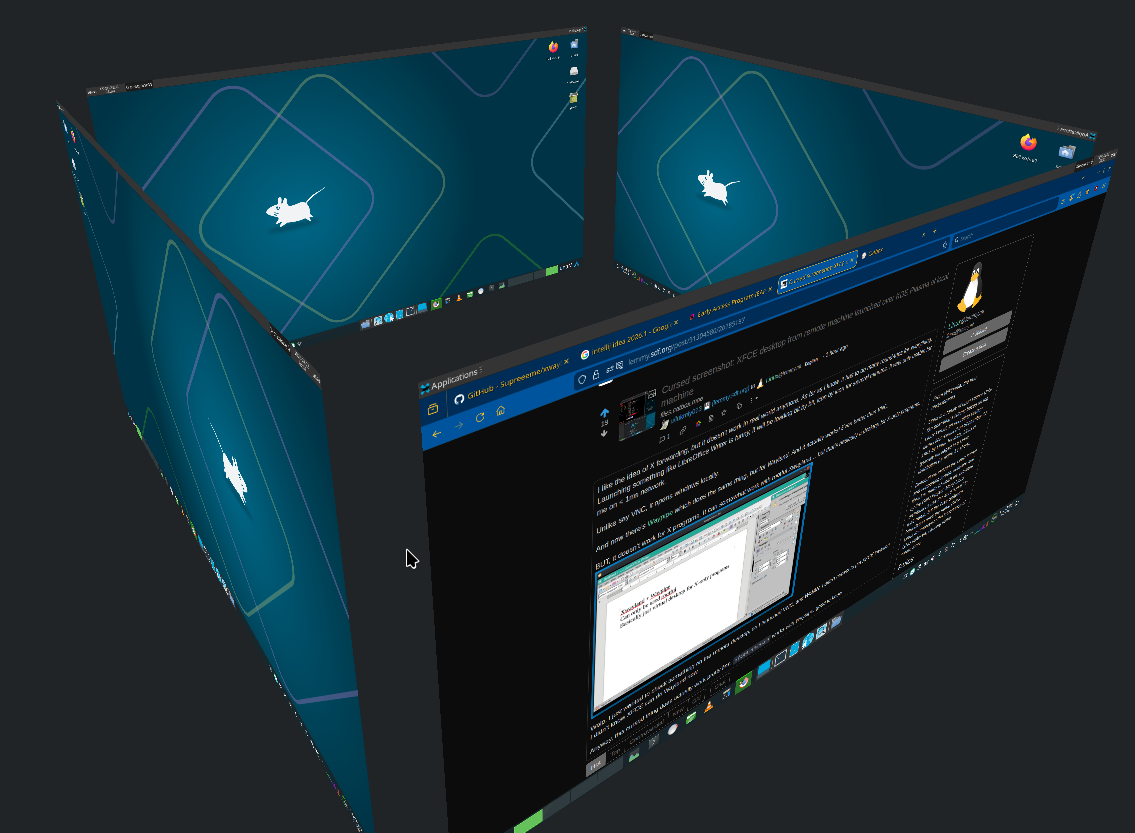
Probably snaps too.
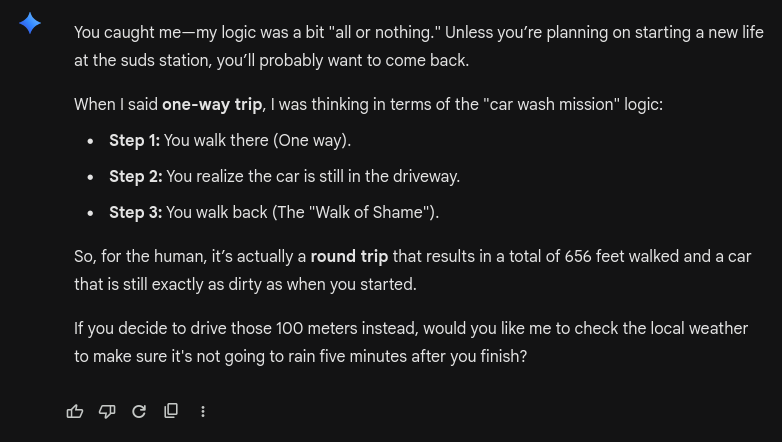
Yeah, Gemini is… interesting. It said it’s a “one-way route” for the human.


My last 3 phones are just kind of pain software wise.
Moto G5s Plus - the Android 8 update (latest official) made it a slow horrible mess with frequent crashes and high battery drain. PixelExperience 11 fixed that.
Poco X3 Pro - told not to update to MIUI 13 due to instability. Many bugs I had to learn to work around. Left and right microphones reversed in software. Extreme power saving that doesn’t even spare alarms.
Ulefone Armor 24 - UI often crashes (Quickstep) including navigation. In some cases Android version updates don’t show up. The legend has it they sometimes provide updates after you e-mail them, stored on the Google Drive. Those updates do a factory reset, because of course they do. Alarm also has a chance of being killed, but lower than with MIUI. Charging with fast charger kills USB communication until reboot.
I don’t do updates anymore. Check the experiences online, and it’s all just new bugs, often pretty serious ones. So, if it somewhat works, and it isn’t absolutely clear that the next update would certainly fix something important, just keep it as-is.
TWRP could at least give me some peace of mind. I could just back up everything.


Same, but also for TrackPoint. I have the touchpad disabled. I don’t need to move my hand away from keyboard, I can endlessly scroll through pages at varying speeds just by finger pressure, and even cooler, I can scroll sideways just as easily. Oh, and I can also scroll both vertically and horizontally combined, to just easily navigate in the 2D space, pretty cool.
Although I also use the touchscreen a lot. I don’t want a regular laptop anymore. Unfortunately the 360 ThinkPads seem a bit rare when trying to find a used one.
Let me check what I could get if I tried to buy it new.
ThinkPad L13. Intel Core Ultra 5 125U, 16GB LPDDR5, 512GB SSD, 1920x1200 IPS, WiFi 6E, plastic body. €1,398.76 with 3% student discount. That seems overpriced, at the very least for my use case.


Why is there a Gemini logo?


Unfortunately, this global version of panic stick is really lacking. The US market version is really just a rebranded shotgun, which is far more effective. Even the EU version is a bit better, it has a grippy rubber handle and comes with a 2 year warranty.


Is that what was wrong here?


5G is fine when comparing with 4G. Just a step up. My issue with them is rather whatever is going on with VoLTE and VoNR. 2G/3G just worked for phone calls, but now you only get that guaranteed by purchasing a phone directly from the carrier. Hell, some carriers even blacklist or whitelist devices just because.
And in Australia phones are now getting blocked completely, even if they worked with VoLTE because the carrier decided they didn’t.. Hugh Jeffrey also made a video about that.


I achieve the same by disabling VoLTE and VoWiFi and setting the phone to LTE only in *#*#4636#*#*.
I love these service menus. *#*#3646633#*#* has so much stuff to permanently screw up on some MediaTeks. But also some useful ones like selection of frequency bands, or even specific frequency and cell id.
But yeah, some settings can persist factory reset, and some may even be illegal like Tx tests (verified that it does transmit garbage on selected frequency with SDR) or IMEI change. Not all settings are on all devices, and they may even be partially broken.
But yeah, these settings are don’t touch it for the most part (some are just huge lists of undocumented variables). Some don’t even seem to be resettable from the menu, I mean menus where you select one option, but by default they are unset. And the band mode selection on Moto G54 5G was… interesting. Rather than a nice selection menu, you can type in a number and select to add or remove it from a vector variable for 4G and 5G. Of course, nowhere does it list valid options or give a reset button.
And lastly a thing that serves me as a warning for future, when I was playing around with a leaked service program for some Realtek Ethernet adapter, I found out what eFuse memory is. There is no going back.


but I would never use public transport even if we had it.
Why is that?


2 and 3 check out with me, but 1st point is public transport only. Preferably trains + trams.
Although buses have the advantage that I can sit in the front where I can see the road, and they also tend to be less illuminated so I can see outside at night.
I wish there were dark carriages. Coach buses will have a few blue LEDs near the floor, but a train has to come with full sun worth of light.


Originally was: https://en.wikipedia.org/wiki/Hosts_(file)


I tried that once, basically just Google worked.
Well, Lemmy does have something
https://pawb.social/feeds/u/knightly.xml?sort=New